CISM Certification: Overview, Requirements, Salary and Jobs
- -
- Time -

CISM, or Certified Information Security Manager, is widely considered among the most prestigious accreditations in information security management. CISM is offered by ISACA, a worldwide organization that is positively oriented to the promotion of IT governance.
The certification is intended for those who design, manage, or audit an enterprise’s information security. This complete reference will explore all you need to understand about the CISM certification, starting with its brief explanation, the qualifications required to obtain it, how much you can earn once you are certified, and the available positions.
Table of Contents
- Overview of CISM Certification
- What is CISM?
- CISM Certification Requirements
- Salary Prospects for CISM Professionals
- Global Salary Trends
- Job Opportunities for CISM Professionals
- Preparing for the CISM Exam
- Detailed Breakdown of CISM Domains
- CISM Certification Maintenance
- Job Market for CISM Professionals
- Advantages of Hiring CISM Professionals
- Conclusion
- FAQs
Overview of CISM Certification
The Certified Information Security Manager (CISM) certification is a globally recognized credential that showcases an individual’s expertise in managing, designing, and overseeing an enterprise’s information security. This overview will delve into the core components and benefits of obtaining the CISM certification, helping professionals enhance their security posture and career trajectory.
What is CISM?
The CISM certification is unique for an individual solely responsible for managing and overseeing an organization’s information security program. Here, it is essential to note that CISM differs from other, generally more technical certifications. It takes a managerial view of information security, including governance, risk, and compliance. This also makes it a good stop on the path to high-ranking IT positions in different organizations.

Benefits of CISM Certification
Industry Recognition
CISM enjoys recognition worldwide and is widely accepted as a benchmark certification for information security management. It helps to improve the overall skill set and knowledge in the information security field, making the certification holder unique in today’s intensely competitive world.
Career Advancement
CISM provides an opportunity to get a job with a higher rank, such as IT manager, security auditor, communications systems analyst, or CIS0. Similarly, it plays an important role for those seeking an essential position in an organization as a professional.
Skill Enhancement
Some of the significant areas covered by the certification include risk management, governance, incident response, and security program development. Such coverage also makes it possible for the certified professional to cope with different security issues because of the broad style of the work.
Networking Opportunities
ISACA membership enables access to other people and related materials concerning the field. This community will afford a venue for the exchange of ideas, development, and other professional benefits.
Start your journey toward becoming a Certified Information Security Manager with the CISM Certification Course with CCSLA.
CISM Certification Requirements
To pursue the CISM certification, candidates must meet a set of stringent requirements designed to ensure they possess the necessary skills and experience. This section outlines the educational background, professional experience, and examination prerequisites required to qualify for the CISM certification, guiding you through the steps to become a certified information security manager.
Eligibility Criteria
To earn the CISM license, prospects must meet specific standards, including:
Experience Requirements
- A minimum of five years of professional work experience in computer security management.
- Experience must be gained within the ten-year time preceding the entry date or within five years from the date of initially passing the test.
Waivers for Experience
Up to two years of experience can be waived for different reasons, such as holding another appropriate certification (e.g., CISSP, CISA, or PMP) or having a degree in information security or a similar area.
Exam Details
- Format: The CISM exam consists of 150 multiple-choice questions.
- Duration: The exam duration is four hours.
- Domains Covered
- Information Security Governance (24%)
- Information Risk Management (30%)
- Information Security Program Development and Management (27%)
- Information Security Incident Management (19%)
- Passing Score: A scaled score of 450 out of 800.
Maintaining CISM Certification
ISACA imposes a CPE hours policy among CISM certification holders that requires one to acquire 20 CPE hours per annum and 120 CPE hours in three years. Further, they must be current with the ISACA membership maintenance fee for the membership year and adhere to the ISACA Code of Professional Ethics.
Salary Prospects for CISM Professionals
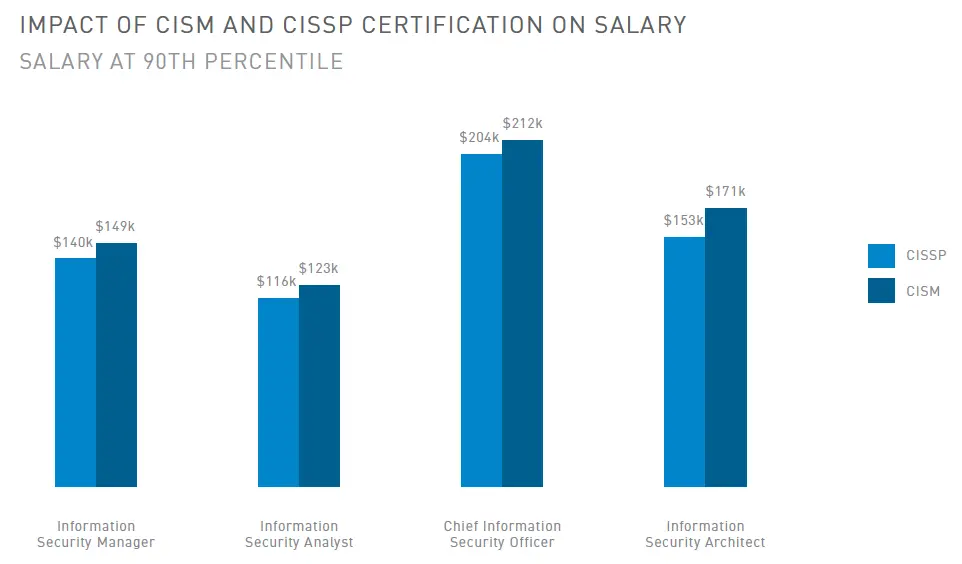
Global Salary Trends
CISM has become one of the most valued certifications in the field of information security, and its holders receive considerable wages. Employment opportunities for security managers are vast and enormous, and CISM certification will hike the salary scale.
Average Salaries by Role
- Information Security Manager: $120,000 – $150,000 per year.
- Chief Information Security Officer (CISO): $150,000 – $250,000 annually.
- IT Audit Manager: $110,000 – $140,000 per year.
- Risk Manager: $100,000 – $130,000 per year.
Factors Influencing Salary
Location
The pay is also relative to the region, with more significant amounts being paid to employees working for tech central firms.
Experience
The experience level in information security management also affects the remuneration expected for the job; employees with more experience are paid highly.
Industry
There are some occupations where salaries are higher; in particular, companies in the finance and healthcare industries are ready to pay more because data security is critical in these industries.
Education and Additional Certifications
Some employers accept workers with other certifications or those with an advanced degree to improve their salary potential.
Boost your career and salary potential with the CISM Certification Course by CCSLA.
Job Opportunities for CISM Professionals
The CISM certification opens doors to a variety of high-demand roles in the cybersecurity field. This section highlights key job opportunities and career paths available to CISM professionals, illustrating the potential for growth and advancement.
Roles and Responsibilities
Candidates holding this certification are well-prepared to take on numerous tasks within the field of information security management.
Key responsibilities typically include:
- EECP: Establishing methods and controls for an enterprise information security program.
- The enforcement of security policies and procedures must be observed here.
- In this case, risk assessments and management imply checking possible risks and planning ways to avoid these risks in the future.
- It is safeguarding the legal requirements the company must meet in light of the laws and regulations governing business operations.
- The second thrust is addressing security incidents and handling the Incident Response Teams.
- It helps to inform an organization’s top management and other stakeholders about security threats and measures.
Popular Job Titles
- Information Security Manager: Supervising and managing security operations at the organization’s central and distributed levels.
- Chief Information Security Officer (CISO): Defining specific information security responsibilities and providing direction at the executive management level.
- IT Audit Manager: Auditing and ensuring that the company subscribes to the internal and external governance standards.
- Risk Manager: Risk management involves locating, evaluating, and minimizing threats to information within the organization.
- Security Consultant: Assisting organizations in formulating the proper measures that need to be taken and the right policies to be implemented to enhance information security.
Industries Hiring CISM Professionals
- Finance and Banking: Data such as financial statements and accounts are categorized as sensitive data that must be protected from the prying eyes of unauthorized personnel and adhere to the legal requirements that have been laid down.
- Healthcare: A guide on the wellbeing of patient information and fulfillment of health information laws.
- Government: Measuring, cataloging, and safeguarding national security data and public sector information.
- Technology: Protecting inventions, ideas, and strategies while assuring the privacy of customers’ information.
- Retail: Data protection measures and averts leakage of consumers’ information.
Preparing for the CISM Exam
Preparing for the CISM exam requires a strategic approach to master the extensive body of knowledge. This section provides essential tips and resources to effectively study and maximize your chances of success on the exam.
Study Materials and Resources
- ISACA’s CISM Review Manual: The original guide covering all test areas.
- Online Training Classes: Interactive classes that provide in-depth information and test preparation.
- Practice Exams: Simulated exams to test your skills and readiness.
- Study Groups and Forums: Joining study groups or internet sites can provide support and ideas from other candidates.
Study Tips
- Understand the Exam Format: Familiarize yourself with the test format and the kinds of questions.
- Focus on High-Weight Domains: Allocate more study time to areas with higher weightage.
- Use Multiple Resources: Combine various learning tools for a complete understanding.
- Practice Regularly: Take practice tests to find weak areas and improve your test-taking skills.
- Stay Updated: Keep informed of the latest trends and changes in information security management.
Get CCSLA’s expert guidance and comprehensive training with the CISM Certification Course.
Detailed Breakdown of CISM Domains
The CISM certification encompasses several core domains, each critical to the role of an information security manager. This section offers a detailed breakdown of these domains, helping you understand the scope and focus areas covered in the certification.
1. Information Security Governance
Focus: Creating and sustaining a security context is necessary to ensure that the information security management plans are aligned with the organization’s goals and meet legal and regulatory requirements.
Key Areas
- Development of an Information Security Strategy and its Management.
- It identifies how information security can be in sync with the goals of an organization.
- The Information Security Governance Framework can be developed.
- These are tasks such as designing security policies, standards, and procedures or establishing other security frameworks.
2. Information Risk Management
Focus: It focuses on goal-oriented information on security risk management for addressing threats and vulnerabilities in organizations.
Key Areas
- Risk management for new products, risk assessment, and monitoring programs.
- It involves tracking and communicating risk management efforts effectively.
3. Information Security Program Development and Management
Focus: The roles it plays include the development of the information security program and the overall responsibility for protecting information assets.
Key Areas
- Establishing an information security program.
- When conducting a risk assessment, key stakeholders and managers of an organization begin integrating security requirements into organizational processes to achieve better organizational security.
- Resource management for security purposes is, therefore, the accomplishment of organizational security objectives by efficiently and effectively utilizing constrained resources in the best manner possible.
- A further goal is to sustain the growth of the information security program.
4. Information Security Incident Management
Focus: It involves creating, implementing, securing, and leading efforts to protect and respond to InfoSec breaches and cyber threats.
Key Areas
- Implementation of a Public Health Incident Management Plan.
- Supervising and organizing the corresponding top-level and detailed functions of incidence.
- Analyzing events after the incident to evaluate effective practices.
- Analyzing and trying to execute improvements based on the learned incidents.
CISM Certification Maintenance
Maintaining your CISM certification ensures your skills remain sharp and relevant. This section explains the continuing education requirements and renewal processes necessary to keep your CISM credential active and recognized in the industry.
Continuing Professional Education (CPE)
To keep the CISM license, workers must stick to ISACA’s CPE requirements:
- Annual Requirement: Earn a minimum of 20 CPE hours annually.
- Three-Year Requirement: Earn a total of 120 CPE hours over a three-year time.
- Care Fee: Pay a monthly care fee.
- Code of Professional Ethics: Comply with ISACA’s Code of Professional Ethics.
Types of CPE Activities
- Educational Courses: Attending or giving applicable courses, workshops, and conferences.
- Professional Meetings: Participating in ISACA local meetings and other industry-related events.
- Contributions to the Profession: Publishing articles, books, or study papers in computer security.
- Self-Study: Engaging in self-study tasks, such as reading applicable texts or workshops.
Ensure your continuous professional development with the CISM Certification Course by CCSLA.
Job Market for CISM Professionals
The job market for CISM professionals is robust and growing, reflecting the increasing importance of cybersecurity. This section explores the demand for certified security managers and the types of roles frequently offered to those with a CISM certification.
Current Trends
Information security management is a rapidly growing field for which most companies seek certified individuals, particularly those who pass the CISM exam. This is because of the increasing instances of cyber threats, data breaches, and privacy violations; there is a need for professionals in security management to formulate and implement proper measures toward increased security.
Geographic Demand
- North America: High demand from technology-related populations such as those in Silicon Valley, New York, and the Washington, D. C. area.
- Europe: More necessities in the financial hubs like London, Frankfurt & Zurich, etc.
- Asia-Pacific: The demand for this certification is increasing, particularly in developing countries like India, China, and Singapore.
- Middle East and Africa: Some other major areas are in big cities like Dubai and Johannesburg.
Industry Demand
- Finance: The financial sector needs strict security standards to safeguard fintech information and data and uphold GDPR and PCI-DSS standards.
- Healthcare: The chief concerns include the privacy of patient information and adhering to the legal requirements for health information, such as the HIPAA legislation.
- Government: Recommendations on how national security data should be managed and the measures that should be put in place to enable it to meet government compliance requirements.
- Technology: Protection of ideas and information on tech business and its clients.
- Retail: While it is true that most consumer information passes through the cloud, it is essential to ensure that these details are highly secured and no data breach is contracted.
Advantages of Hiring CISM Professionals
Hiring CISM-certified professionals offers distinct advantages, including enhanced cybersecurity expertise and improved risk management. This section examines how CISM credentials add value to organizations by bolstering their security posture and compliance capabilities.
Expertise in Information Security Management
The CISM designation places holders in good standing to professionally oversee sound information security programs’ development. This way, it becomes possible to safeguard an organization’s information and also have a means of handling any hacking incident.
Strategic Perspective
CISM certification involves an approach to security that addresses issues about security goals in the commerce of a firm. This perspective aids in maintaining a balance between security and organizational objectives while providing a framework that aligns security with organizational strategies and goals.
Leadership and Communication Skills
CISM professionals are also expected to be able to communicate the potential risks of the business and security solutions to the management and other stakeholders. This article identified that their leadership skills help them manage security teams and coordinate security activities in the organization.
Compliance and Risk Management
Professionals who sit for the CISM accreditation have sufficient knowledge and understanding of compliance measures and risk management techniques. They must assist organizations in managing regulatory considerations in more formalized contexts and identify risk management strategies that will reduce security threats.
Conclusion
This certification has far-reaching benefits that boost the career destination of an individual in information security management. Both general and specialized training not only affirm the knowledge and competence one possesses but also provide opportunities for higher-paying careers and managerial positions in different fields.
Are you ready to consider CISM as your next career step? Join the CISM Certification Course and acquire everything to help you work efficiently in this exciting sector.
FAQs
CISM (Certified Information Security Manager) is a certification offered by ISACA (Information Systems Audit and Control Association) that focuses on information security management. It is designed for IT professionals responsible for managing, developing, and overseeing information security systems in enterprise-level applications, or who manage a team of IT security professionals.
The CISM certification is intended for information security managers, aspiring managers, or IT consultants who support information security program management. It is especially beneficial for IT professionals looking to transition into managerial roles within the cybersecurity field.
To obtain the CISM certification, candidates must pass the CISM examination, possess at least five years of work experience in information security with at least three years in information security management roles, and agree to adhere to ISACA’s Code of Professional Ethics.
The CISM exam covers four primary domains: Information Security Governance, Information Risk Management, Information Security Program Development and Management, and Information Security Incident Management. These domains encompass a broad range of knowledge and skills needed to manage, design, and oversee an enterprise’s information security.
The cost of the CISM exam varies depending on whether or not you are a member of ISACA. For members, the exam fee is typically around $575, while for non-members it is approximately $760. Prices may vary slightly by location and are subject to change.
Salaries for CISM-certified professionals vary widely depending on the job role, years of experience, and geographic location. On average, CISM-certified professionals can expect to earn between $100,000 and $160,000 annually. This certification often leads to high-paying roles due to the critical nature of the skills and knowledge confirmed.
CISM-certified professionals are well-qualified for high-level roles such as Chief Information Security Officer (CISO), Information Security Manager, Security Consultant or Analyst, IT Audit Manager, and Security Auditor. These roles involve overseeing the information security of an organization, developing security strategies, and managing teams of security professionals.
The CISM certification is valid for three years. To maintain the certification, holders must earn and report 120 Continuing Professional Education (CPE) credits over a three-year period and pay an annual maintenance fee. At least 20 CPE credits must be earned each year.
The CISM certification recognizes an individual’s expertise and competency in managing enterprise information security teams. It provides credibility to a professional’s resume, often leading to higher employment prospects, promotions, and salaries. It also ensures that certified professionals are updated with the latest information security practices and standards.
Study materials for the CISM exam can be found through various sources, including the official ISACA website, which offers study manuals, review courses, and practice tests. Additionally, there are many third-party providers that offer training courses, books, and online resources designed to help candidates prepare for the exam.






