What is Shimming in Cyber Security? Types, Attack & Defense
- -
- Time -

Cybercrime is ramping up to break new records in 2023, with estimates pointing to 33 billion accounts being breached – that works out to a staggering 2,328 violations per day, or 97 cyber victims every single hour. So far, a whopping 800,000 cyber attacks have been logged to date, meaning hackers are carrying out strikes every 39 seconds around the clock.
These alarming stats drive home the cold hard truth – cyber threats are blowing up, and we need to wise up to tools like shimming that allow criminals to sneak in, rip off data, and cash in big.
This article will delve into what is shimming in cyber security, difference between skimming and shimming, how shim attacks work, and, most critically, how to guard your organization against shimming attack security threats. By getting savvy to shimming risks, you can gain the edge against cybercrooks looking to pull a fast one on your network security.
- Understanding Shimming in Cybersecurity
- How Shimming Attacks Work
- Types of Shimming Attacks
- Signs and Symptoms of Shimming Attacks
- Preventing and Detecting Shimming Attacks
- Keeping software and operating systems up to date
- Installing reputable antivirus and anti-malware software
- Being cautious of Phishing attempts
- Regularly monitoring online accounts for suspicious activity
- Utilizing anti-shimming technology
- Tools and software that can help prevent shimming attacks
- Employee training and awareness to counter shimming attacks
- Difference between Shimming and Skimming
- Importance of Protecting Against Shimming Attacks
- Steps to Enhance Cybersecurity Measures Against Shimming Attacks
- Shimming and Its Relevance to Different Cybersecurity Technologies
- Case Studies: Examples of Shimming Attacks
- 2. The German Cyberattack
- Conclusion
- FAQs
Understanding Shimming in Cybersecurity
Shimming attacks are blowing up as a sneaky way for cybercriminals to slip past security and sink their claws into systems. But what is shimming in cyber security?
Shimming refers to an attack where hackers shove in a snippet of malicious code called a shim to intercept data and potentially take control. Shims wiggle their way into software at the kernel level, making them hard to pick out. Once nestled in, shims can grab onto API calls, modify information, and open backdoors for attackers to creep in.
Shimming attacks come in different forms:
- Data Theft: Shimming opens the door for thieves to siphon off sensitive info like usernames, passwords, and credit cards as data passes between software. Shims slip in between components, letting attackers eavesdrop and scrape valuable data flowing through the system.
- Malware Insertion: Shimming can also pave the way for more extensive attacks by letting criminals shove malware deep into target environments. Once embedded, the malware can spread, opening backdoors for bad actors to creep in and take control.
No matter the type, Shimming gives hackers eyes and ears inside systems and security.
How Shimming Attacks Work
Shimming attacks follow a sneaky step-by-step process to rip off credit card details from ATMs and pumps. Here’s how thieves cash in:
Step 1: Thieves using a chip called “shim”
Shimming starts with cybercriminals getting their hands on a teeny shim chip to worm into the payment system. These tiny chips cram in a microprocessor like a small computer brain, along with flash memory to stash swiped data.
Step 2: Placing a chip on an ATM or user’s card
Next, attackers have to fiddle with the payment system to stick on a shim card reader. This device latches onto the real card reader to swipe and copy account information.
Step 3: Hiding the chip
To avoid detection, thieves sneak a plastic cover over the PIN pad. This makes the system look normal while the shimmed pad eavesdrops on PINs typed in.
Step 4: Stealing card details
Finally, shimmers wedge another chip over the card slot to scrape and store everything on the magnetic stripe as users dip their cards.
Step 5: Misusing stolen information for personal gain
Once shimmers have lifted enough account data, they use or sell it online to rip others off and reap profits.
Shimming relies on sly physical tampering to worm inside payment systems unnoticed. Stopping these attacks requires vigilance to spot and shut down any suspicious devices before thieves can take advantage.
Types of Shimming Attacks
1. Advanced Persistent Threat Shim
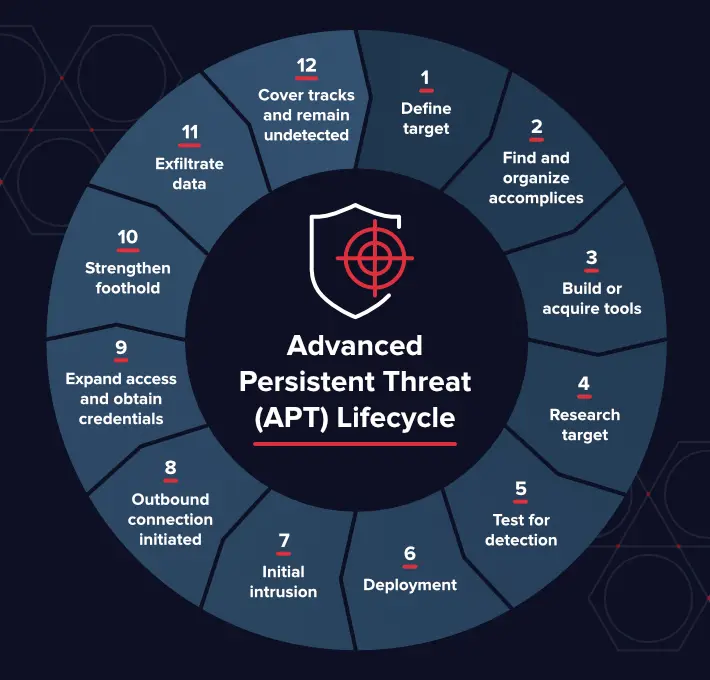
Advanced persistent threats (APTs) have the chops to zero in on specific users based on their roles or access to dig up valuable data. APTs can worm their way into networks and lurk undetected while siphoning off intelligence.
Even before an attack, they may already have backdoors propped open on compromised machines to take control when the time is right.
These sophisticated threats also have the technical know-how to whip up stealthy rootkits and remote access tools to dig their claws in deep, avoiding detection.
With multiple command and control options, APTs can pivot to maintain their grip even when defenses boot them out.
Some of the slippery tactics APTs leverage include:
- Planting multiple strains of malware that slither in under the radar.
- Setting up various C2 destinations to hop between if one gets shut off.
- Using off-net updates and VPN malware to sidestep monitoring.
- Leveraging zero-days and unique attacks specifically crafted to break through defenses.
- Continually tweaking approaches to skirt past antivirus detection.
Back in 2008, the World Bank ditched a third-party service provider after digging up evidence their systems were used to shimmy malicious code into the bank’s network.
Investigators uncovered that spyware, specifically a keystroke logger, had been slipped into computers at the bank’s Washington D.C. headquarters. All signs pointed to the vendor’s contractors as the likely culprits that fiddled with the systems to stick on the spyware.
This shady software worming around was siphoning off info as employees typed away. The spyware helped the attackers eavesdrop on activities and tunnel deeper into the network to siphon off sensitive data.
This real-world case highlights the havoc APTs can wreak when they weasel their way into target systems. Even trusted third parties can be leveraged as a backdoor for stealthy attacks.
2. Browser-in-the-Middle Shim
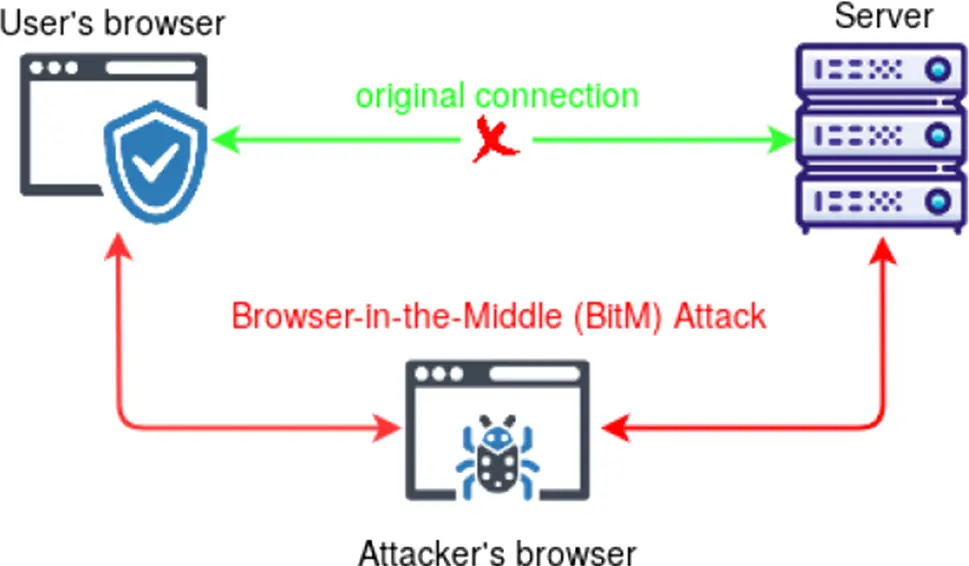
Browser-in-the-Middle (BitM) attacks aim to secretly insert themselves between a victim’s browser and the intended web service to spy on communications. Here’s how they play out:
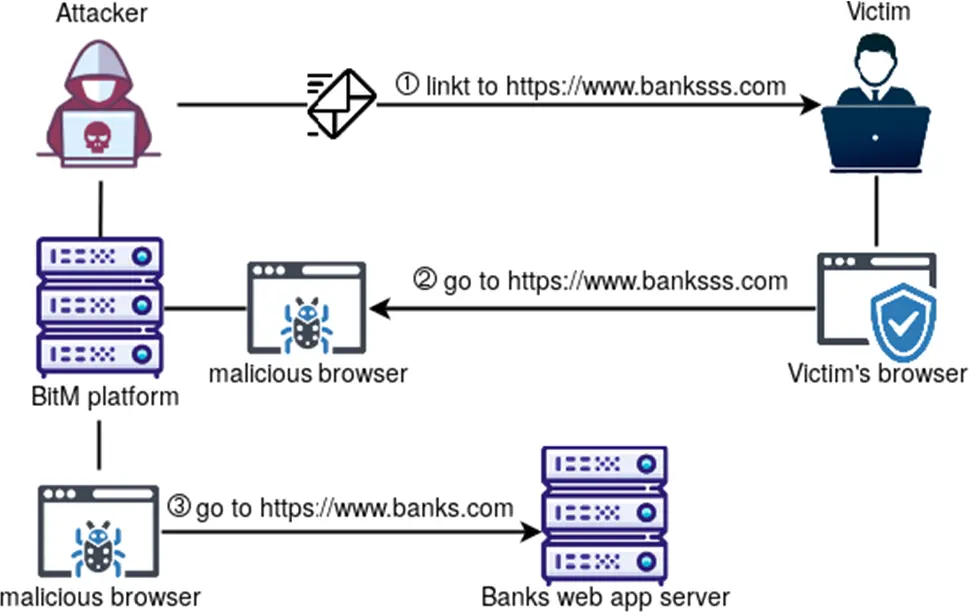
First, the attacker has to lure the target into clicking on a trick link that funnels them to the attacker’s server hosting a rigged web browser. Phishing techniques like spoofed emails are often used to bait the trap.
Once the victim takes the bait and clicks through to the malicious browser, it essentially takes over the session. The rogue browser sets up an encrypted tunnel between itself and the real application while hiding its presence.
From this man-in-the-middle vantage point, the attacker can now eavesdrop on all input and data as the user interacts with the web app, thinking everything is normal.
The rogue browser proxies all activity through the attacker’s server, allowing them to record, manipulate, and siphon off anything transmitted between the victim and the web service. This lets them intercept credentials, session tokens, emails, and more.
Even if the web application uses HTTPS encryption, the attacker’s server decrypts traffic before passing it on to the victim’s browser. The user is none the wiser as the malicious browser imitates the real thing while spying mercilessly in the background.
Signs and Symptoms of Shimming Attacks
Shimming attacks are sneaky by nature, but they leave behind telltale signs if you know what to look for. Here are some red flags to watch out for:
1. Unexpected Pop-Ups
If brand new pop-up windows start popping up out of nowhere, shims could be worming their way in. Shims latch onto normal processes and hijack them to open dodgy new browser windows.
Sudden pop-ups to sketchy sites can point to shims trying to phone home or download more malicious payloads.
2. Altered Browser Settings
Another sign of a shim is if your browser settings mysteriously get tampered with. Cybercriminals use shims to sneak in and change configurations like your homepage and default search engine.
Keep an eye out for any settings that get altered without your knowledge, as it could indicate an unwanted shim.
3. Unusual Account Activity
Finally, increased activity in online accounts, like new logins from odd locations, can also demonstrate a shim sniffing around. Once embedded in your network, shims can latch onto your credentials and data. Be suspicious of any abnormal behavior that suggests an outsider is tunneled into your accounts.
By learning the typical red flags, you can spot potential Shimming activity before the attackers dig too deep. Promptly flush out any suspect shims to keep them from sinking their claws into your system.
Preventing and Detecting Shimming Attacks
The following precautions can help you lock out shims before they latch on:
Keeping software and operating systems up to date
Continuously update programs and operating systems to squash vulnerabilities. Hackers exploit holes in outdated software to shimmy their way in. Patch promptly to shut the door.
Installing reputable antivirus and anti-malware software
Antivirus and anti-malware software can sniff out and block known Shimming tactics. Make sure to keep these defenses up-to-date to catch the latest threats.
Being cautious of Phishing attempts
Stay vigilant against Phishing attempts, which deploy traps to trick users into letting shims slip through. Avoid clicking suspicious links and attachments that can embed shims.
Regularly monitoring online accounts for suspicious activity
Keep a close eye on online accounts for any red flags like new devices or locations. This can reveal a shim worming its way in to scrape credentials.
Utilizing anti-shimming technology
Advanced Anti-Shimming solutions can provide vital protection against these sneaky attacks. With robust Anti-Shimming capabilities woven throughout your defenses, you have a much greater chance of catching shims in their tracks and locking them out for good.
Tools and software that can help prevent shimming attacks
Specialized tools, such as File integrity monitoring software, Memory scanners, API monitoring tools, and Network traffic analyzers, can aid in shoring up defenses against Shimming by spotting telltale signs of tampering.
Here are some softwares to prevent Shimming attacks:
- LifeLock
- NordLayer
- Malwarebytes
- Bitdefender Total Security
Employee training and awareness to counter shimming attacks
Educate staff on warning signs like unusual pop-ups so they can report potential shims early. Employee awareness is key for a proactive defense.
With layered security measures, you can catch Shimming threats before they take hold. Diligence and quick response are essential for locking out attacks before the damage is done.
Difference between Shimming and Skimming
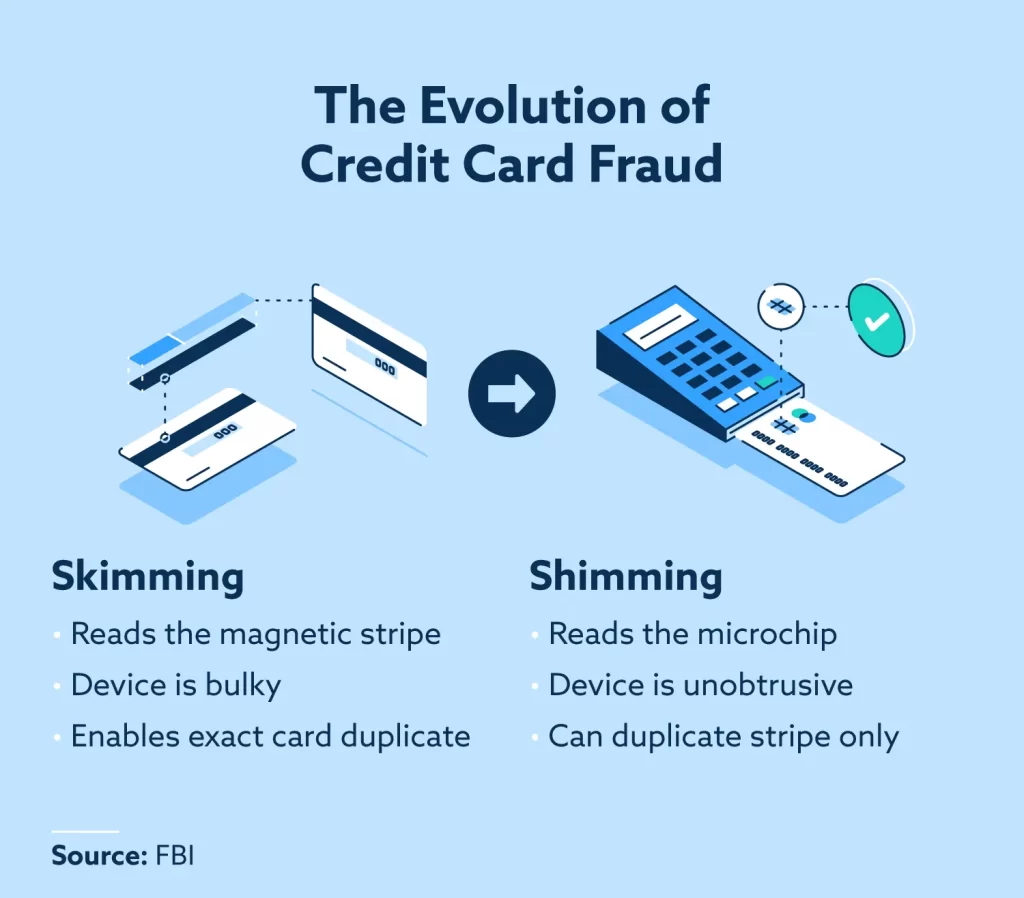
The difference between Skimming and Shimming may sound similar, but they use different techniques to siphon off your data:
Skimming
Skimming has been around for ages as a way for fraudsters to latch onto payment systems. Skimmers are physical devices that are crafted to worm their way into card readers and freeload off real transactions.
Typically skimmers are clipped on externally, where they can eavesdrop on users swiping their cards through magnetic stripes. They grab card data and PINs entered, storing it or transmitting it wirelessly so criminals can cash in later.
Skimmers are essentially parasites that leech off payment systems to scrape data. Their external attachments make them relatively easier to spot through physical inspections.
Shimming
Shimming takes a sneakier approach by infiltrating payment systems from the inside out. Tiny shim chips are designed to slide right into the hardware like chip card readers, where they can blend in seamlessly.
Once firmly planted inside, shims tap into the inner workings to infiltrate transactions. As users dip EMV chip cards, shims intercept communications and funnel data out to criminals through backdoor channels.
Because shims integrate directly into hardware, they are extra stealthy. Tamper-resistant designs, robust monitoring, and regular testing are key to exposing shims before they sink their claws in.
While both target payment systems, Shimming’s deeper integration and smaller footprint give it an edge in stealth and scraping card data. Defenders need to be on guard against both breeds of payment system predators.
Here is a comparison table contrasting skimming and shimming:
|
Aspects |
Skimming |
Shimming |
|
How it Works |
External devices attached to the payment system to intercept stripe data |
Malicious chips inserted into payment hardware to compromise chip readers |
|
Target Data |
Magnetic stripe data |
Chip/EMV data |
|
Install Method |
Clipped on card readers externally |
Inserted inside card readers |
|
Footprint |
Larger external attachments |
Small internal hardware |
|
Data Transmission |
Retrieved manually |
Often transmitted wirelessly |
|
Timeline |
Longstanding method |
Relatively newer technique |
|
Detection Difficulty |
Easier to spot as external attachments |
Harder to detect when inside the system |
Importance of Protecting Against Shimming Attacks
Shimming attacks may fly under the radar, but underestimating their impact leaves you wide open to data theft and fraud. Here’s why organizations must make Shimming protection a top priority:
Impact on personal and financial information
Once a shim attack takes hold in a system, there is little stopping attackers from tunneling in deep and getting their hands on sensitive personal data. From their embedded vantage point, shims can latch onto all kinds of information transmitted between interfaces and memory.
Usernames, passwords, account numbers, social security digits, birth dates, contact info, and more all get soaked up by shims as transactions occur. The shims can either store scraped data locally for criminals to come collect or siphon it off in real-time via backdoor channels.
Consequences of falling victim to shimming attacks
With stolen financial information in hand, attackers can easily clone cards, raid accounts, and ring up fraudulent charges before owners catch on. The monetary damage can be massive.
Stolen data often winds up for sale on dark web markets, fueling broader cybercrime. The shady ecosystem flourishes off your losses.
Steps to Enhance Cybersecurity Measures Against Shimming Attacks
Here are bullet point steps to enhance security against Shimming attacks:
- Keep systems patched and updated to shut the door on vulnerabilities shims exploit to slither in. Don’t give them an easy opening.
- Install Anti-Shimming and Anti-Tampering technologies to pinpoint and block attacks targeting payment systems and APIs.
- Deploy robust endpoint security with behavioral monitoring to sniff out subtle signs of shims worming their way onto hosts.
- Enable strong access controls and least privilege policies, so shims can’t tunnel deeper into networks when they latch on somewhere.
- Monitor networks proactively for signs of data exfiltration that could indicate a shim phoning home with stolen data.
- Inspect payment hardware regularly for any evidence of physical tampering or modifications that hint at shim installations.
- Test systems and validate integrity to reveal any unauthorized alterations indicative of shims worming inside.
Shimming and Its Relevance to Different Cybersecurity Technologies
Delving into the nuanced world of cybersecurity, ‘shimming’ emerges as a pivotal technique with far-reaching implications across various technologies. Let’s explore its significance.
Shimming in the context of antivirus software
Antivirus software aims to sniff out and block malware, but Shimming presents some unique challenges for traditional AV tools:
- Signature-based AV focuses on known threat signatures. But shims often leverage zero-day attacks or unique code specifically designed to fly under the radar.
- Behavior-based AV looks for suspicious activity that could reveal a shim worming its way in. But shims are stealthy by nature, making them hard to pinpoint.
- Shims bury themselves deep in memory or chip firmware beyond the view of standard AV scans targeting files and applications.
- Encrypted tunnels allow shims to phone home and exfiltrate data without being detected by AV network monitoring.
While AV has a role in multi-layered security, its blind spots mean shims can still slip by unnoticed.
Role of shimming in firewalls and intrusion detection systems
Firewalls and intrusion detection systems (IDS) face limitations in identifying and blocking Shimming threats:
- Network firewalls focus on blocking external threats. But shims typically worm their way into internal networks by compromising hardware within the perimeter.
- Once inside, shims can phone home to external C2 servers using encrypted channels. Firewalls let this encrypted traffic slip through as ‘normal’.
- Behavior-based IDS has the best shot at spotting subtle signs of shims communicating or siphoning data. But tuning is required to pinpoint Shimming specifically.
- Anti-tampering defenses integrated into IDS can help reveal hardware compromises or firmware modifications indicative of shims.
- Sandboxing, honeypots, and deception tools also help lure and detect shims when they latch onto traps mimicking real data and assets.
While firewalls and IDS aid in defense, their perimeter-focused nature gives shims an edge.
Interaction between shimming and encryption technologies
Encryption plays a critical role in security, but Shimming attacks take advantage of blind spots:
- Encryption secures data in transit and at rest through techniques like SSL/TLS and drive encryption.
- From their embedded position, shims can latch onto unencrypted card data and account info before it gets encrypted for transit elsewhere.
- Shims may also sniff out encryption keys or certificates to decrypt data that is transmitted or stored encrypted.
- Tamper-resistant encryption apps and hardware security modules prevent shims from sinking their claws into the encryption process itself.
- Multi-layer encryption across devices, software, and the network makes it exponentially harder for shims to hit the jackpot by compromising just one layer.
Case Studies: Examples of Shimming Attacks
1. The Naval War College Attack
This real-world incident exposed the damage that state-sponsored hackers can inflict when they manage to infiltrate sensitive government networks. Chinese cyber threat actors were pinpointed as the perpetrators who carried out the attack on the Naval War College network.
They managed to tunnel their way deeper into military systems once inside, eventually compromising over 12,000 Pentagon networks and 5 million connected devices, according to officials.
Intelligence sources were able to trace the malicious activity back to a sophisticated Chinese state-sponsored hacking group that had code-named these network infiltration operations “Titan Rain.”
The incident laid bare the reality that even the most sensitive government systems are still vulnerable if stealthy attackers find a way to tunnel in through security layers.
The fallout was immense, with military operations disrupted, data potentially stolen, and an entire branch forced offline until the threats could be contained.
2. The German Cyberattack
In 2007, German officials discovered that hackers based in China had tunneled their way into a wide swath of government ministry computer systems. They did so by embedding spyware inside trojaned Microsoft Office files that allowed the malware to be installed when users accessed the tainted documents.
Once firmly entrenched inside the networks, the hackers were siphoning off sensitive data on a daily basis, amounting to 160 gigabytes of stolen information before German cybersecurity personnel managed to detect the attack and cut off the data heist.
Domestic intelligence agencies traced the hacking activities back to groups in several Chinese provinces that were believed to be carrying out these cyberspy operations at the behest of the Chinese military.
To cover their tracks, the hackers had rerouted their malicious traffic through intermediary computers based in South Korea. But their tactics were still uncovered.
The breach set off alarms that China likely had wormed its way into German corporations as well to steal intellectual property and technology secrets in order to turbocharge their own economic growth at the expense of Germany.
Conclusion
Shimming represents a slippery new cyber threat that organizations must get savvy to.
Luckily, understanding the shimming attack security landscape arms defenders with the insight needed to lock these threats out.
With vigilance and proactive precautions, enterprises can gain the upper hand against shimmers trying to weasel their way in for financial gain. While shimming may allow hackers to operate temporarily in the shadows, dragging these threats into the light will ensure they have nowhere left to hide.
Feeling in the Dark About the Growing Threat of “Shimming” Attacks? CCS Learning Academy understands the struggle and has designed a comprehensive CISSP Exam Preparation Course.
With seasoned experience in the cybersecurity education field, CCS Learning Academy aims to provide the ultimate training experience. Interested professionals looking to earn this gold-standard certification can visit the website to learn more and enroll.
Organizations don’t need to let shimming catch them off guard any longer. This course equips teams with the knowledge to get a handle on these slippery threats. Enrolling now is the key to mastering shimming defense.
FAQs
1. What is shimming in the context of cybersecurity?
Shimming refers to an attack where hackers insert a piece of malicious code, known as a shim, to intercept data and potentially gain control. Once in place, shims can intercept API calls, modify information, and open backdoors for attackers.
2. How does a shimming attack work?
Shimming attacks involve a step-by-step process where cybercriminals use a shim chip to infiltrate payment systems, eavesdrop on PINs, and steal card details. Once they gather enough data, they misuse it for personal gain.
3. What are the types of shimming attacks?
The two main types discussed are Advanced Persistent Threat Shim, which zeros in on specific users based on their roles, and Browser-in-the-Middle Shim, which secretly inserts between a victim’s browser and the intended web service.
4. How can we detect shimming attacks?
Some signs of shimming attacks include unexpected pop-ups, altered browser settings, and unusual account activity. Being aware of these red flags can help in identifying potential shimming activity.
5. How can we defend against shimming attacks?
Defense measures include keeping software updated, installing reputable antivirus software, being cautious of phishing attempts, monitoring accounts for suspicious activity, and utilizing advanced anti-shimming technology.
6. What’s the difference between shimming and skimming?
While both target payment systems, skimming involves external devices attached to payment systems, whereas shimming involves malicious chips inserted directly into payment hardware.
7. Why is it essential to protect against shimming attacks?
Shimming attacks can lead to significant data theft and fraud. Once a shim is in place, cybercriminals can access sensitive personal and financial information, leading to significant monetary and reputational damage.
8. What cybersecurity technologies are affected by shimming?
Shimming presents challenges for traditional antivirus tools, firewalls, and intrusion detection systems. It also interacts with encryption technologies, often taking advantage of their blind spots.
9. Are there any real-world examples of shimming attacks?
Yes, notable incidents include the Naval War College Attack and the German Cyberattack, highlighting the scale and impact of such threats.






