What Is Baiting in Cyber Security? Examples, Techniques & Prevention
- -
- Time -

It was a typical Saturday morning when I opened my email. As I sipped my morning coffee, scanning through the usual promotions and newsletters, one email subject line grabbed my attention – “Claim Your Free Vacation Now!” My curiosity piqued, and I clicked to open the email without a second thought. That one harmless click opened the floodgates to a relentless cyberattack that consumed my whole weekend. Little did I know, I had just taken the bait from a clever baiting scheme.
Have you ever taken the bait and clicked on a shady link or downloaded a suspicious file? If so, you may have fallen victim to a cyberattack technique called “baiting”. This crafty ploy lures users into traps by playing to their curiosity or offering something enticing.
Baiting has hooked many unsuspecting internet users, allowing cybercriminals to access valuable personal data or access devices and networks. Once the bait has been bitten, the outcomes can range from identity theft to malware infections to full-system hacks.
In this article, we will dive deeper into the bait used in these cyber schemes, the various baiting techniques employed, and most importantly, what internet users can do to avoid getting caught on the phisher’s line. We’ll uncover real-life baiting attempts so you can spot red flags before taking a bite of anything fishy online. With some insight and preventative measures, you’ll be able to wriggle free if baited and keep your information safe rather than getting dragged into hot water.
- What Is Baiting in Cyber Security?
- Examples of Baiting Techniques
- Infamous Real-world Baiting Incidents
- FAQs
- Q1: What is baiting in cyber security?
- Q2: How does baiting differ from other social engineering techniques?
- Q3: Can you provide examples of baiting attacks?
- Q4: What are some common techniques used in baiting attacks?
- Q5: How can individuals recognize and avoid baiting scams?
- Q6: What are the potential consequences of falling for a baiting scam?
- Q7: Are businesses or individuals more targeted in baiting attacks?
- Q8: What measures can businesses take to prevent baiting attacks?
- Q9: How effective is antivirus software in protecting against baiting attacks?
- Q10: Can baiting occur on social media platforms?
- Q11: What role does employee training play in preventing baiting attacks in organizations?
- Q12: Are there any legal repercussions for falling victim to a baiting attack?
What Is Baiting in Cyber Security?
“Phishing” cyberattacks have been around for years, but baiting takes the deception one step further by offering internet users something tempting to incite engagement. The “bait” comes in many forms – a provocative or curious file, a tantalizing link, an attractive image, a “free gift”, or even the promise of access to unauthorized data. This bait plays into human impulses and drives like greed, vanity, righteous indignation, voyeurism, or simply a desire for the forbidden fruit.
Once the bait has been bitten, the hacker can then carry out exploits like malware installation, data/identity theft, account takeover, or network infiltration.
The key aspect that sets baiting apart from other schemes is that the unsuspecting target consciously chooses to bite the bait and actively enables the malicious activity themselves. For example, they make the decision to download and execute malware masquerading as video software or steal data left tantalizingly out in the open.
The bait must look legitimate and appealing enough to trigger that fateful click that sets the hook. So hackers get into the psychology of what internet users find irresistible based on trends, current events, human drives, and more. Then, they weaponize that temptation to drag victims into compromised positions.
Some baits floated by hackers are seemingly innocent at face value but conceal barbed hooks that snag users who let curiosity get the better of them. However, many baits cross ethical lines, intending to tempt targets into actively enabling cybercrimes. We’ll uncover some prime examples of different baiting techniques next.
Examples of Baiting Techniques
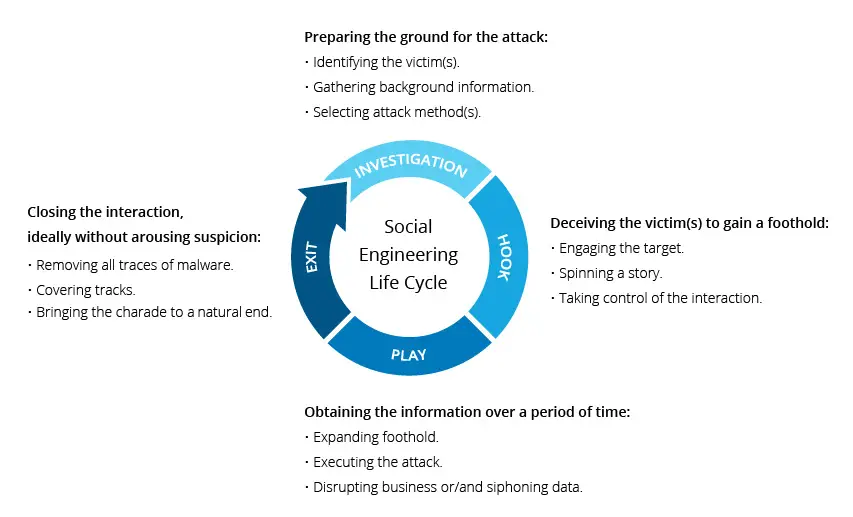
Cybercriminals dangle different types of tantalizing “bait” to hook victims into enabling data theft, malware delivery, and infrastructure access. We’ll reel through real examples like phony free offer lures, malware download traps, and infected physical devices that played upon human curiosity to breach organizations.
Tempting Offers Bait
The tantalizing lure of free stuff is nearly irresistible to most internet denizens. Our inboxes are inundated with deals, gifts, contests, and giveaways galore, with some offering amazing prizes or products without spending a dime. But we need to apply extra scrutiny, or we may get sucked into a baiting scam.
Cybercriminals regularly blanket email lists with freebie offers to rope in as many bites as possible. The temptation may come in the form of free phone or gift cards, chances to win big prizes, free software or game giveaways, exclusive content access, or coupon deals. The messages often appear credible, linking to websites mimicking legitimate brands. But it’s a bait with a hook.
Once users click through to claim their freebies, they soon find themselves caught on the fraudster’s line. The sites ask for personal information like names, emails, addresses, and phone numbers to register an account or confirm eligibility. Victims willingly hand over the data, at which point their identities become compromised. Hackers can then unleash phishing schemes, steal financial data, hack accounts, and more using this intel.
In other freebie scams, users must download files or enable web extensions to unlock software or content. By agreeing, they unintentionally download malware directly onto their device. This ushers in a host of new threats like data encryption, remote access, mining cryptocurrency, and botnet conscription.
The lures seem innocuous and sometimes even legitimate at the surface level. But make no mistake – users who bite on free offers, more often than not, end up getting reeled into fraudulent schemes. It pays dividends to carefully vet promotions, contests, gifts, and giveaways to ensure no hidden thorns exist underneath the rosy exterior.
Malware Download Bait
Another breed of internet bait comes in the form of questionable website downloads, promising users free access to premium entertainment content and software. Music, movies, games, and apps don’t grow on trees – so how can random sites provide endless media for free? By baiting illegal media seekers into enabling cybercriminal exploits instead.
The internet harbors various illicit websites offering paid music, films, programs, and more without charge. Many oblivious users happily bite at the chance to score free stuff, heedless of darker ulterior motives. After spending hours scouring forums and dodging pop-up carnage, they finally download the long-sought freebie.
Unfortunately, rather than quality media, what often ensues is an underhanded bait-and-switch. The downloaded files contain malware payloads ranging from info-stealing Trojans to network-hijacking bots. Some variants encrypt user data files until ransom demands are met. Others conscript the hacked computer into botnets controlled by remote attackers.
By striving to hook media freeloaders, cybercrooks instead compromise victims’ devices and data. What’s more, accessing illicit download hubs is generally illegal regardless of the outcomes. But baiting banks on the idea that users won’t be able to resist the lure of temptation. And once they bite, there is often no going back from the snap of the trap.
The appeal of scoring free media motivates compromised actions; meanwhile, hackers bank on this to infect unsuspecting downloaders’ devices. The bait offers treasures at surface level but really just delivers an undercurrent of trouble.
Malware Delivery Bait
Technology users understandably proceed with caution regarding email attachments, understanding malware’s prevalence. Thus, cybercriminals have concocted an insidious baiting evolution – infected external devices delivered to targets’ physical mailboxes.
This brand of attack, dubbed “evil maid”, plants nefarious USB or hard drives equipped with malware payloads. Attackers then rely upon human curiosity to trigger infection. The booby-trapped devices often land on recipients’ actual doorsteps, left conspicuously in public venues, or sent via post.
When discovered, the strange parcel instantly raises questions. What resides on this mysterious drive? It could contain secret corporate files, useful tools, amusing images – or just benign documents. But that potential for confidential content or insight proves irresistible. So victims connect the unknown drives, and the hidden hack unfolds.
The malware payload rapidly infects the host system and then utilizes remote access tools to communicate with command servers. From there, cybercriminals can exfiltrate data, corrupt files, deliver additional malware, or pivot to attack wider networks.
And users willingly enabled it, enticed by the prospect of scandalous or restricted content. The hackers played to innate human curiosity regarding potentially important data. By package-delivering Trojan hardware, attackers created a targeted infection vector that appealed to recipients’ inquisitive instincts.
In this manner, baiting strikes at the heart of human motivation – the thirst for information. And victims ultimately sanction the ploys by physically unleashing hazards onto their own systems. Evil maids highlight social engineering’s role in priming ideal baiting conditions.
Tips to Avoid Baiting Attacks
Don’t get sucked into social engineering traps! Learn techniques to identify and steer clear of baiting pitfalls. We’ll share actionable advice on resisting urgency pressure, training staff on threat recognition, safely verifying links, and staging security simulations to inoculate reflexes.
Stay Alert to Avoid Being Hooked
Cybercriminals rely on the principle that haste makes waste. They spring traps using time pressure, emotions, and hasty decision-making to hook victims. Receiving surprising news, fabulous offers, or alarming alerts clouds judgment, prompting snap actions that hand the advantage to attackers. However, users can avoid being reeled in by slowing down reaction time upon suspicious contacts.
Many fraudulent schemes demand immediate action or response under false pretenses. Phony alerts may warn that account access will soon expire, trying to elicit panic responses that surrender credentials or data. Bogus freebie offers often have extremely limited claim periods, hoping users will bite quickly without deeper consideration. Cybercrooks realize playing off emotions like fear, greed, or curiosity elicits hastier engagement with less skeptical scrutiny.
However, these high-pressure scenarios themselves indicate likely bait. Authentic organizations rarely demand instant responses prior to verifying user identity. Users should be wary of any unsolicited contacts trying to compel swift actions or input. Rather than rushing to react, take time to cautiously verify legitimacy. Check sender addresses, hover over embedded links to preview destinations, research offer origins, and consult others to determine validity.
Resisting the urge for snap judgment prevents being hooked by social engineering schemes. By slowing reaction time, weighing options, and scrutinizing context, users have the opportunity to identify baits before biting. Cybercriminals leverage human impulsiveness, but can be thwarted by level-headed evaluation of contact motives prior to further engagement.
Educate Employees to Swim Safely
People often click links, install software, and access files with minimal understanding of risks. Like swimming in waters with lurking predators, a lack of awareness turns users into prey for lurking cyber exploits. However, with proper training on dodging bait tactics, employees become digitally-savvy swimmers prepared to identify and avoid traps.
Begin with core knowledge – what constitutes baiting and phishing attempts? Ensure personnel recognize tactics like urgent requests, questionable links, odd attachments, and suspicious offers. Provide examples of phony alerts mimicking banks or webmail services demanding account verification. Share news of actual malware incidents resulting from tainted downloads. The more informed workers are on attack trends and warning signs, the less likely they’ll take the bait.
Next, conduct practical exercises to reinforce secure habits. Launch simulated phishing attempts mimicking hacker behavior to gauge susceptibility rates. Implant USB sticks containing benign scripts that trigger alerts when opened to monitor human curiosity. Award prizes to employees exhibiting avoidance behaviors for motivation.
Actual web-based cyber range environments also provide immersive education on modern social engineering schemes. Equipped with current threats knowledge and avoidance training, personnel become vital human firewalls shielding themselves and the organization from harm.
Education elicits a well-informed first line of defense against attacks. Whereas ignorance spreads damage, informed employees represent fundamental barriers to preventing organizational data breaches and malware outbreaks. Providing continuous awareness resources and practical training minimizes attack vulnerabilities modern hackers prey upon.
Verify Links to Avoid Following Fraudsters
As digital environments house infinite connections, users rely upon links to navigate to intended destinations. However, blindly trailing links without verification hands control to potentially untrustworthy guides. Skilled hackers disguise, mimic, and falsify links to misdirect victims and conceal attack software. To manage risk exposure from weaponized links, users should validate actual endpoints prior to clicking.
Embedded links provide zero transparency by default – without closer inspection, users cannot confirm destinations or intentions. Instead of immediately clicking and enabling redirects, first, hover cursors over links to reveal precise URL callouts. Scan notations, assessing domain names, paths, and files for legitimacy. Search engines verify the current reputation of landing sites. Any signs of spoofing, odd syntax, third-party domains, or recent creation may indicate fraudulent links leveled to capture traffic.
Also consider source context – emails, posts, and documents with spelling/grammar issues or other quality concerns warrant extra scrutiny of all embedded links. Unfamiliar sender addresses should clue users against blindly believing the validity of any associated hypertext. And high-value individuals like executives present attractive targets for identity impersonation, demanding confirming contact authenticity.
Following links facilitates cybercriminal objectives by driving traffic, spreading malware, and stealing data. But users focused on verifying redirect destinations deny hackers control of where victims navigate to. Cultivating consistent practices for probing links first fortifies everyday digital travels.
Test Defenses Via Simulations
Social engineering exploits prey upon normal human vulnerability to lies, fear, uncertainty, and doubt. However, running realistic attack simulations helps strengthen instinctive reactions to malicious attempts. By safely exposing personnel to mimicked schemes, organizations inoculate workforces against compromising behaviors while gauging prevention capabilities.
IT departments can safely stage mock ransomware, phishing, and bait attacks reflecting current threat tactics. Penetration testers use cloned malware variants and fashion authentic-looking lure documents to effectively copy hackers minus real payloads.
Employees undergoing these immersive threats may initially fall victim like any civilian user. However, observing peers being hooked itself packs an impact, prompting self-reflection on avoiding similar fates.
Post-exercise surveys should collect participant feedback on which threat indicators or persuasive tactics proved most influential. Did brevity, threats of account suspensions, or gift offers primarily trigger impulsive reactions? Were typed hyperlinks more effective than attached documents? This human perspective data fuels continuous education on employees’ behavioral weak points most leveraged by hackers.
Running recurring stimulation events keeps threat recognition instincts sharp long-term. Training regimens updated with contemporary attacker techniques ensure personnel are responsive to emerging exploits. Mapping exercises to seasonal phishing spikes or public malware outbreaks connect directly to real unfolding campaigns. The more simulations reflect current realities, the better-prepared workforces become.
Guard Against Infection with Antivirus Solutions
Voluntarily consuming or installing mysterious files brings severe risk of injecting system-compromising malware. Once active inside hardware or networks, cyber pathogens spread rapidly – extracting data, encrypting files, and hijacking device control. However, modern antivirus solutions provide proactive safeguards against malicious code threats.
Updating antivirus software with the latest definitions ensures recognition of the newest attack malware variants by matching code signatures. Heuristic analysis also identifies suspect behaviors like unusual filesystem modifications or suspicious network calls to block undiscovered strains. Cloud connectivity shares verified threat intelligence across customer endpoints to provide widespread immunity.
Protection features like email attachment sandboxing contain malicious documents from tampering systems by isolating code execution. Web content filtering prevents accessing known malware-hosting sites attempting drive-by downloads. Some solutions even intercept harmful links sent via messaging apps for phones and tablets.
For deeper defense, application whitelisting strictly limits software execution to administrator pre-approved binaries only. Banning all unrecognized code effectively stops code injection attacks relying on bait victims into running unverified downloads. Added endpoint detection and response (EDR) services further analyze system-wide event logs to identify indicators of active malware intrusions.
Rather than rely on low-security awareness among users as the last line of defense, InfoSec teams should intelligently harden networks against inevitable human mistakes. Deploying robust antivirus solutions and proactive defenses makes progress difficult for successful malware footholds. And endpoint visibility assists faster containment when isolated infections still occur.
Infamous Real-world Baiting Incidents
Major headlines often loom large thanks to high-profile cyber incidents involving bait. We’ll uncover stunning social engineering tricks like fake virus guidelines on weaponized drives hooked healthcare firms and phony Google alerts that breached Democrats’ communications. These real baiting cases illustrate cunning plays on social context to lower victim suspicion before striking.
Hackers Cast Phony HHS Lures to Infect US Firms
In times of crisis like pandemics, hackers leverage public fear and uncertainty to lower defenses. So when the COVID-19 health emergency gripped global attention in 2020, cybercriminals worked feverishly to exploit the situation. State-sponsored hackers and financially-driven crime rings alike fashioned coronavirus-themed attacks to ensnare victims. And in 2022, the notorious FIN7 group hooked various US organizations using phony virus guidance as cover for infecting systems with ransomware.
The cyber cartel distributed parcels containing booby-trapped USB flash drives to multiple companies, primarily those within the defense contracting and IT services industries. The first round mimicked Department of Health and Human Services postal mail, citing updated COVID-19 guidelines to prompt insertion into workstations. The second parcel imitated an Amazon gift box with a $50 Best Buy gift card, incentivizing the recipient to view files on the accompanying USB.
Once inserted into computers, the drives weaponized a variant of the BlackMatter ransomware to encrypt local network files for extortion. The group demanded ransoms up to $5 million paid in cryptocurrency to supply decryption keys. The attack also employed “BadUSB” exploits to rapidly spread itself. This technique reprograms USB flash drive firmware to masquerade as a keyboard upon connection. It then autonomously types advanced hacking commands, enabling deeper network access to exacerbate damage.
FIN7 baited recipients by providing extremely timely lures reflecting current events to lower suspicions just enough. Riding public preoccupation with pandemic guidance and restricting commerce, the group fished successfully for a pathway into corporate networks. And victims themselves triggered the infections by voluntarily connecting the weaponized drives. The scheme proved so successful that the FBI issued a specific warning against the attack type to spark increased vigilance.
Phony Security Lure Hooks Democrats’ Emails
Political races often devolve into no-holds-barred contests, but the 2016 US presidential election set new lows for campaign trickery. Russian intelligence hackers notoriously breached the email systems of the Democratic National Committee (DNC) using fraudulent security warnings as cover. The stolen messages proved severely damaging upon public release, turning the election into a world-influencing event.
Seeking to unsettle the DNC and aid opposing Republican candidates, advanced persistent threat APT29 spent over a year infiltrating networks through tactical social engineering. The team impersonated legitimate Google alerts, sending phishing emails reporting “suspicious attempts to sign in” to personal accounts. The messages urged verifying account credentials on an embedded link to thwart unauthorized access.
Clicking the believable security alert opened a decoy Google sign-in page collecting usernames and passwords. Unwitting recipients entered their Google account details, not realizing the fake page enabled account takeover by the phony “security assistant”. The hackers gained full access to read the contents of users’ Gmail mailboxes, including years of sensitive DNC communications regarding campaign strategies and political maneuvers.
By June 2016, the schemers leaked 20,000 compromised Democratic National Convention emails detailing their candidate vetting processes and fundraising plans. The communications revealed bias against primary challenger Bernie Sanders, prompting DNC leadership resignations. But the greatest damage was the reinforcement of controversy plaguing the Democrats’ presidential nominee. As the media examined more stolen documents daily, the leaks became an albatross no PR response could overcome, contributing to electoral loss months later.
A complex foreign influence operation used a single deceptive phishing email to trigger an email security meltdown that affected global politics for years following. Despite no evident flaws in software defenses, human engineering of stolen trust enabled unprecedented access and unforeseen consequences still reverberating today.
Slack Impersonation Opens Floodgates to Uber’s Systems
Modern digital environments require authenticating users to prevent anonymous access and build organizational trust in identity verification. However, threat actors specialize in forging or stealing credentials that duplicate legitimate user permissions. By impersonating actual insiders, these infiltrators gain trusted status, enabling extensive access with minimal scrutiny. As rideshare leader Uber discovered in 2022, compromised identities provide golden tickets into tech infrastructures through sheer borrowed credibility.
An attacker compromised an internal Uber employee’s Slack account through undetermined means, though social engineering was likely involved. By hijacking the worker’s credentials, the actor gained trusted access to Uber’s communications platform. They used this ill-gotten insider status to canvas network identities, pivoting between apps and roles in search of greater privileges. The threat actor ultimately accessed a wide swath of cloud storage buckets and databases harboring sensitive customer data, financial figures, and code repositories.
The culprit announced the epic hack by posting an explicit photo of a male body part on a public Uber Slack channel frequented by engineers. Despite this immature red flag drawing global attention, the infiltrator retained access for a full day before being booted from corporate systems. During this lengthy tenure, massive amounts of proprietary data were pillaged, though Uber could not determine the full impact scope following the incident.
Uber’s reliance on access controls for security proved fatally flawed once a single identity was compromised. Though the worker’s account hijacking occurred through unconfirmed means, social engineering likely enabled the password theft. The lasting result was an identity joyride granting the culprit keys to entire IT kingdoms. Uber learned the hard way that access management alone fails against attacks abusing borrowed credentials – deeper monitoring and controls become vital.
Conclusion
Baiting demonstrates the power of weaponized temptation and deception in the realm of cybersecurity. The variety of lures and delivery tactics cybercriminals employ highlight social engineering’s position as the most effective attack vector endangering organizations.
As we explored in depth through real-life examples, baiting takes many forms – tantalizing offers, illegal media downloads, poisoned devices, and more. No sector remains immune from these socially-derived exploits playing to human curiosity, fear, or vice. The resulting infections, data breaches, and infrastructure hijacks lead to steep financial loss and reputation damage.
However, businesses can break this grueling cycle via both technology hardening and human fortification. Patching software flaws, leveraging antivirus defenses, practicing suspicion of unsolicited offers, and verifying contacts all minimize exposure. However lasting success requires regular end-user education and updating personnel on the latest criminal tactics and containment procedures.
Equipping workforces with cybersecurity understanding must extend across the enterprise to accounting, HR, logistics, and support roles alongside IT. Comprehensive learning platforms like CCS Learning Academy prepare all employees to identify and withstand bait situations through awareness of underlying psychological triggers behind attacks. Role-specific bundles provide precisely tailored social engineering training, solving vulnerabilities unique to each department.
In the escalating cyberwar, the high ground belongs to proactive defenders constantly reinforcing infrastructure and sharpening human detection capabilities. With comprehensive cybersecurity awareness education from CCS Learning Academy, organizations can empower users to recognize and refuse baited traps across the evolving threat landscape.
FAQs
Q1: What is baiting in cyber security?
Answer: Baiting in cyber security is a type of social engineering attack where an attacker lures a victim into a trap to steal personal information, infect their system with malware, or gain unauthorized access. The bait often comes in the form of a seemingly attractive offer or item that piques the victim’s curiosity or greed.
Q2: How does baiting differ from other social engineering techniques?
Answer: Baiting differs from other social engineering techniques like phishing or pretexting in that it specifically involves offering something enticing to the victim as a lure. While phishing often relies on fear or urgency, baiting entices the victim with the promise of a reward or benefit.
Q3: Can you provide examples of baiting attacks?
Answer: Common examples of baiting include offering free music or movie downloads that contain malware, USB drives left in public places that are loaded with malicious software, and fake free offers on websites that lead to malicious sites or prompt for personal information.
Q4: What are some common techniques used in baiting attacks?
Answer: Techniques include creating legitimate-looking ads or pop-ups offering free goods or services, sending emails with attachments that claim to be something of interest, and physical baiting like leaving malware-infected flash drives in areas where they can be easily found.
Q5: How can individuals recognize and avoid baiting scams?
Answer: To avoid baiting scams, be wary of offers that seem too good to be true, avoid downloading files or clicking on links from unknown sources, use updated antivirus software, and never plug unknown USB drives or other hardware into your devices.
Q6: What are the potential consequences of falling for a baiting scam?
Answer: Consequences can include malware infection, data theft, financial loss, identity theft, and compromise of personal or corporate security. In a corporate environment, it can lead to significant breaches and loss of sensitive information.
Q7: Are businesses or individuals more targeted in baiting attacks?
Answer: Both businesses and individuals can be targeted in baiting attacks. Attackers may target individuals to gain access to personal data or financial accounts, while businesses are targeted for corporate espionage, data breaches, or financial gain.
Q8: What measures can businesses take to prevent baiting attacks?
Answer: Businesses can implement strict security protocols, conduct regular employee training on recognizing and responding to social engineering attacks, use advanced malware detection and prevention tools, and enforce policies for handling external media
and devices.
Q9: How effective is antivirus software in protecting against baiting attacks?
Answer: Antivirus software can be effective in detecting and preventing malware associated with baiting attacks, especially if the software is regularly updated. However, since baiting also involves social engineering, user awareness, and caution are equally important for complete protection.
Q10: Can baiting occur on social media platforms?
Answer: Yes, baiting can occur on social media platforms. Attackers may use fake profiles to send enticing offers, links to malicious websites, or infected files through social media messages or posts.
Q11: What role does employee training play in preventing baiting attacks in organizations?
Answer: Employee training is crucial in preventing baiting attacks. Regular training sessions can educate employees about the nature of these attacks, how to recognize them, and the appropriate actions to take if they encounter a potential baiting scenario.
Q12: Are there any legal repercussions for falling victim to a baiting attack?
Answer: While being a victim itself may not have direct legal repercussions, a baiting attack can lead to data breaches or security incidents that may have legal consequences, especially if sensitive or regulated data is compromised. Organizations may face fines, lawsuits, or regulatory actions if they fail to protect data adequately.






